The convergence of Information Technology (IT) and Operational Technology (OT) in Industrial Automation and Control Systems (IACS) has resulted in the significant extension of the industrial threat landscape with the risks inherent in IT, including cyberattacks. The ISA/IEC 62443 is a set of standards and practices that serve as a comprehensive framework for IACS cybersecurity management to address and mitigate these risks.
The ISA/IEC 62443 series has been developed by the ISA99 committee of the International Society of Automation (ISA) and adopted by the International Electrotechnical Commission (IEC). The ISA99 committee ensures that the ISA/IEC62443 standards are consistent with the more general ISO-27000 series of cybersecurity standards issued by the International Organization for Standardization (ISO).
The ISA/IEC 62443 family of standards (and the associated technical reports designated with a TR prefix) are organized by target audience and align with IACS lifecycle phases. The security requirements mandated in the standards provide firm guidance for all stakeholders of the IACS lifecycle.
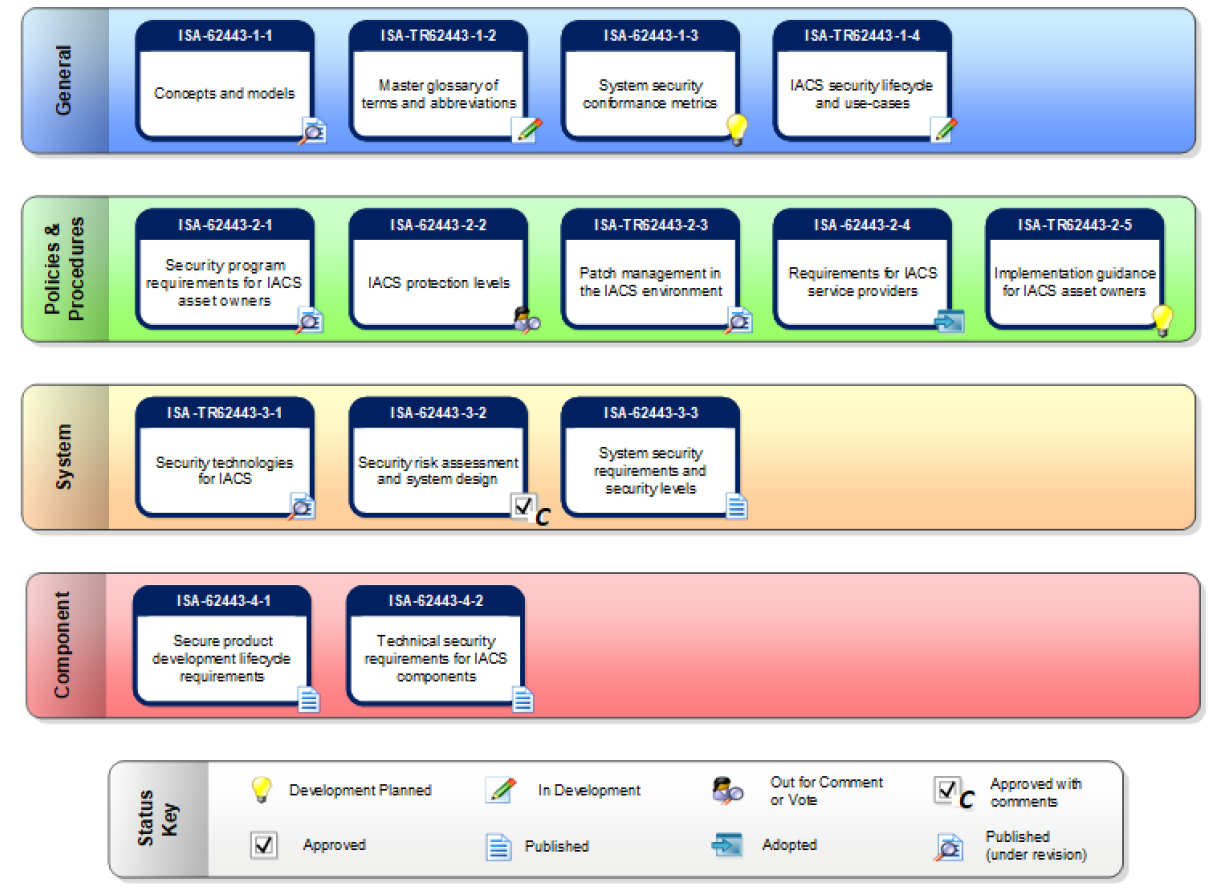
The diagram below, courtesy of ISA, displays the various products in the ISA/IEC 62443 series of IACS standards and technical reports.
The IACS Stakeholders
The IACS stakeholders span a wide range of people, from suppliers to integrators and asset owners. To establish a robust and effective IACS cybersecurity, all stakeholders share responsibility during all phases of the IACS cybersecurity life cycle.
- Product suppliers must develop secure-by-design components. These components should include security capabilities to support the use of the products in integrated solutions.
- System integrators must use site-specific security best practices to support the cybersecurity requirements for the deployment of products at operational sites.
- Asset owners must configure, deploy, operate, and maintain the solution in compliance with the approved cybersecurity guidelines.
IEC 62443 Principles
IEC 62443-1-1 defines an Industrial Automation and Control System (IACS) as a “collection of processes, personnel, hardware, and software that can affect or influence the safe, secure and reliable operation of an industrial process.”
The following principles are the pillars of the IEC 62443 standards:
- IACS cybersecurity is an ongoing process and not a one-time goal.
- The IACS components must be secure-by-design.
- The integration of IACS components into an industrial environment is mandated and supported by defense-in-depth policies and practices.
Overview of ISA/IEC 62443 family of standards
ISA/IEC 62443-4-1, Product Security Development Life-Cycle Requirements, specifies the requirements for developing secure-by-design IACS products. The standard also defines a secure development lifecycle for the development and maintenance of these products’ security. The development lifecycle includes guidelines and practices for a “birth-to-death” management of product development:
- Security requirements definition
- Secure-by-design
- Secure implementation (including coding guidelines)
- Product verification and validation
- Defect management
- Patch management
- Product end-of-life
These security requirements apply only to the developers and maintainers of a product for developing, maintaining, and retiring IACS hardware, software, or firmware.
Effectively managing all IACS lifecycle phases is vital because of the impact cyber risks and challenges present to operational reliability and the interrelation between all IACS components. In every case, the recommended cybersecurity responses should address people, process, and technology.
ISA/IEC 62443-4-2, Security for Industrial Automation and Control Systems: Technical Security Requirements for IACS Components, provides the cybersecurity technical requirements for components, such as embedded devices, network components, host components, and software applications. The standard defines security capabilities that enable an element to mitigate cyber risks and threats while operating at a specific security level without employing additional countermeasures.
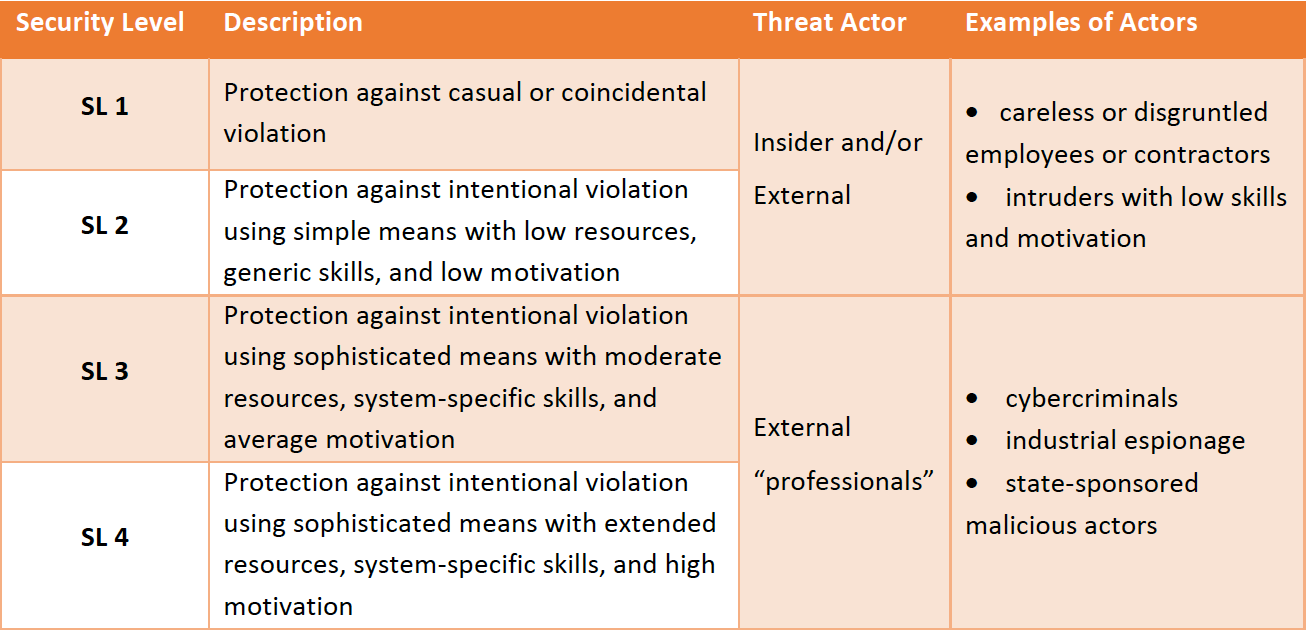
ISA/IEC 62443-3-3, System Security Requirements and Security Levels establishes the security assurance levels of the IACS components. These security assurance levels guide the required cybersecurity functions to increase robustness and make the products resistant to cyber threats. The table below presents an overview of the four security levels described in detail in ISA/IEC 62443-3-3.
Product suppliers should offer IACS components with designed cybersecurity capabilities. If the suppliers cannot ensure the component’s cybersecurity level, the integrator or solution provider is at risk, spending valuable resources on mitigation and imposing IACS design constraints. The deployed solution may also be fragile, making patch and vulnerability management ineffective and leaving the system open to threats. Further, defense-in-depth strategies may become challenging if the IACS components are not free from known vulnerabilities and robust against network attacks.
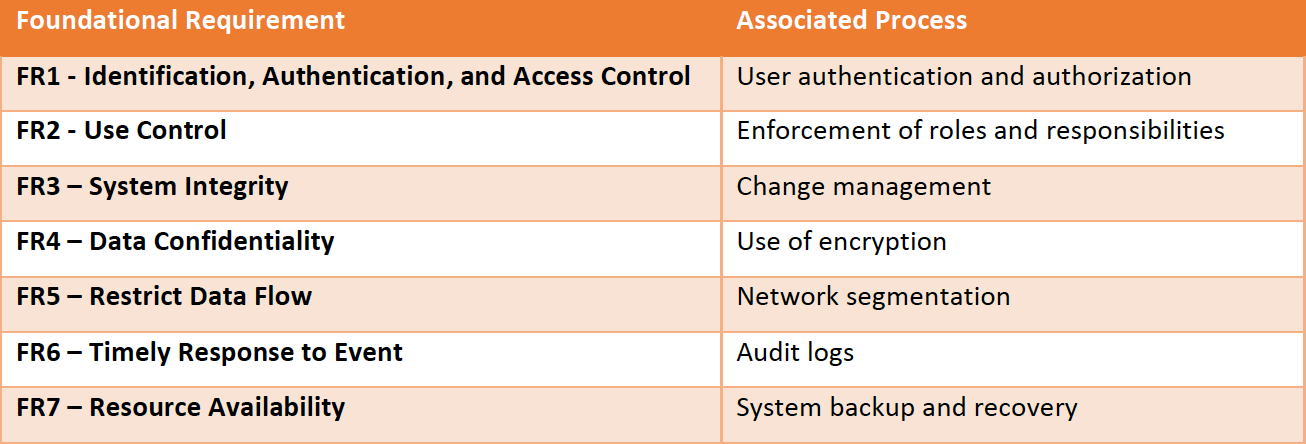
IEC 62443-3-3 also defines the foundational security requirements, described in the table below:
ISA/IEC 62443-3-2, Security Risk Assessment, System Partitioning and Security Levels, considers that effective IACS cybersecurity is a matter of proper risk management. Each IACS component presents a different risk to an organization depending on:
- The threats it is exposed to
- The likelihood of those threats being exploited
- The inherent vulnerabilities in the system
- The consequences of a compromised system.
For these reasons, ISA/IEC 62443-3-2 defines a set of engineering measures to guide organizations through the process of assessing the cyber risk of a particular IACS component and identifying and applying security controls to reduce that risk to organization-specific tolerable levels. The standard provides the foundation for specifying cybersecurity countermeasures aligned with the target security level and the capabilities defined in ISA/IEC 62443‑3‑3.
Benefits for all stakeholders
The ISA/IEC 62443 family of standards presents benefits for all IACS stakeholders.
The product suppliers and integrators rely on internationally accepted, objective, cost-effective IACS cybersecurity requirements, reducing the friction caused by the use of various requirements across regions or industry sectors.
End-users benefit from the foundational and broad IACS cybersecurity knowledge and experience codified into the standards. The use of the ISA/IEC 62443 standards for framing procurement requirements augments staff capabilities for establishing robust cybersecurity policies, procedures, and measures.
How ORIGNIX helps
ORIGNIX delivers bespoke cybersecurity engineering services for inherently safer design and operation of industrial processes. We utilize systematic cyber and operational risk assessment using well-established techniques and templates. Our cyber Process Risk Assessment (cyberPRA) methodology is based on ISA/IEC 62443 and IEC 61511 industry standards. The assessment identifies potential gaps, hazards, vulnerabilities, independent protection layers associated with engineered industrial processes at plant facilities. The identified cyber risks are prioritized based on realistic cost-benefit analysis.
To learn how our customers benefit, visit our website.