HOW WE DELIVER
ORIGNIX Cyber Operational Resilience Management (cyberORM™) system is a market differentiator and our crown jewel methodology. The framework maps the ISA/IEC 62443 cybersecurity life cycle with ISA/IEC 61511 functional safety life cycle and the IT Infrastructure Library (ITIL) best practices in managing security and changes to network-capable devices within Industrial Automation and Control Systems.
The industry-first cyberORM™ system operates as the day-to-day beating heart of the ISA/IEC 62443 aligned IACS cybersecurity life cycle. It addresses the daily challenges in a structured and systematic way under well-defined Capability Maturity Model Integration (CMMI) key capabilities.
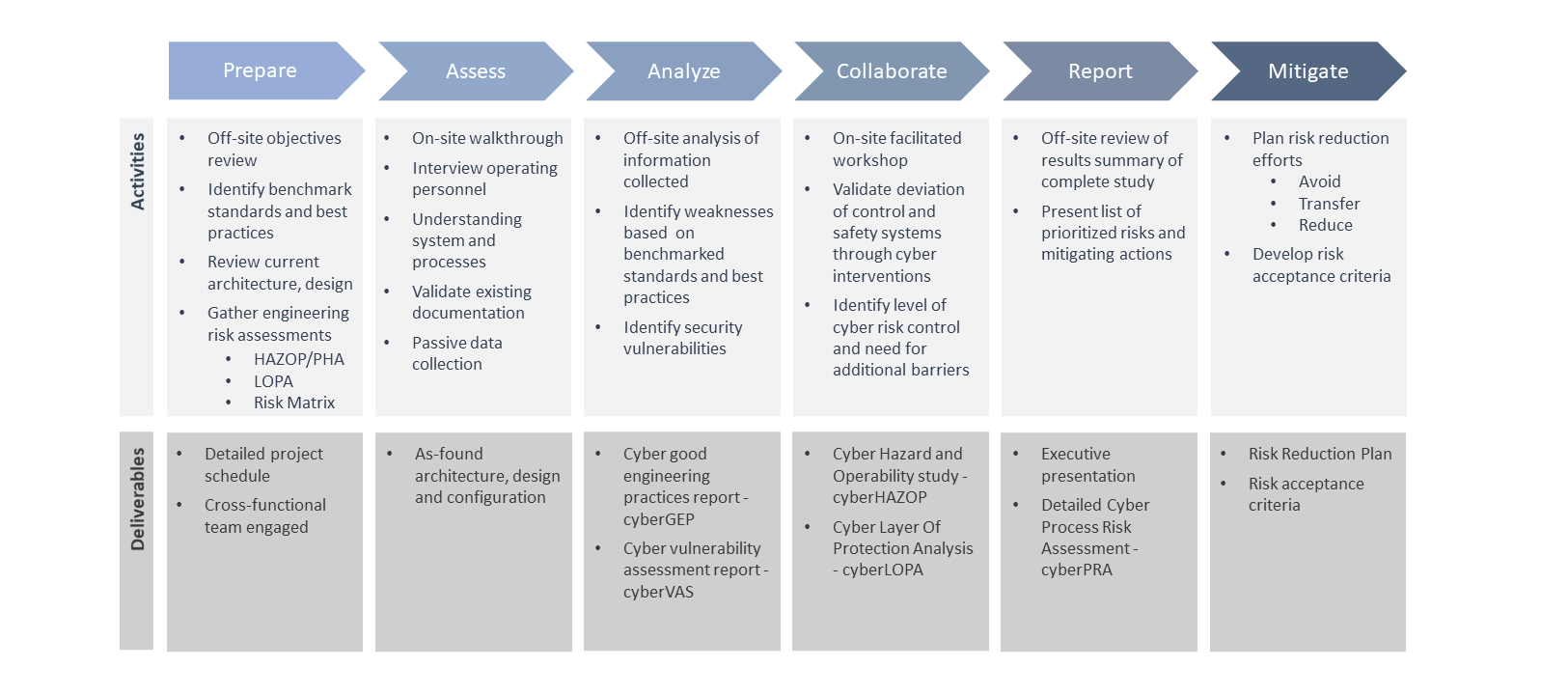
CyberPRA™ STUDY
The CyberPRA™ project is delivered through a six-phase approach:
Phase 1: Prepare. Assessment of the project objectives, review of current architecture design, configuration information, HAZOP, PHA, and risk matrix.
Phase 2: Assess. On-site vulnerability assessment (cyberVAS™).
Phase 3: Analyze. Off-site cyberGEP™ assessment, threat and vulnerabilities analysis.
Phase 4: Collaborate. Collaborative on-site sessions:
- cyberHAZOP™ – Evaluation of threats, consequences, countermeasures, and discussion of recommendations.
- cyberLOPA™ – Evaluation of high consequence incident scenarios. Order of magnitude estimation of cause frequency, loss event, and safeguards.
Phase 5: Report. Development of executive summary and detailed report. Presentation of the prioritized list of risks and actions.
Phase 6: Mitigate. Development of requirements specifications. Risk reduction planning and execution.
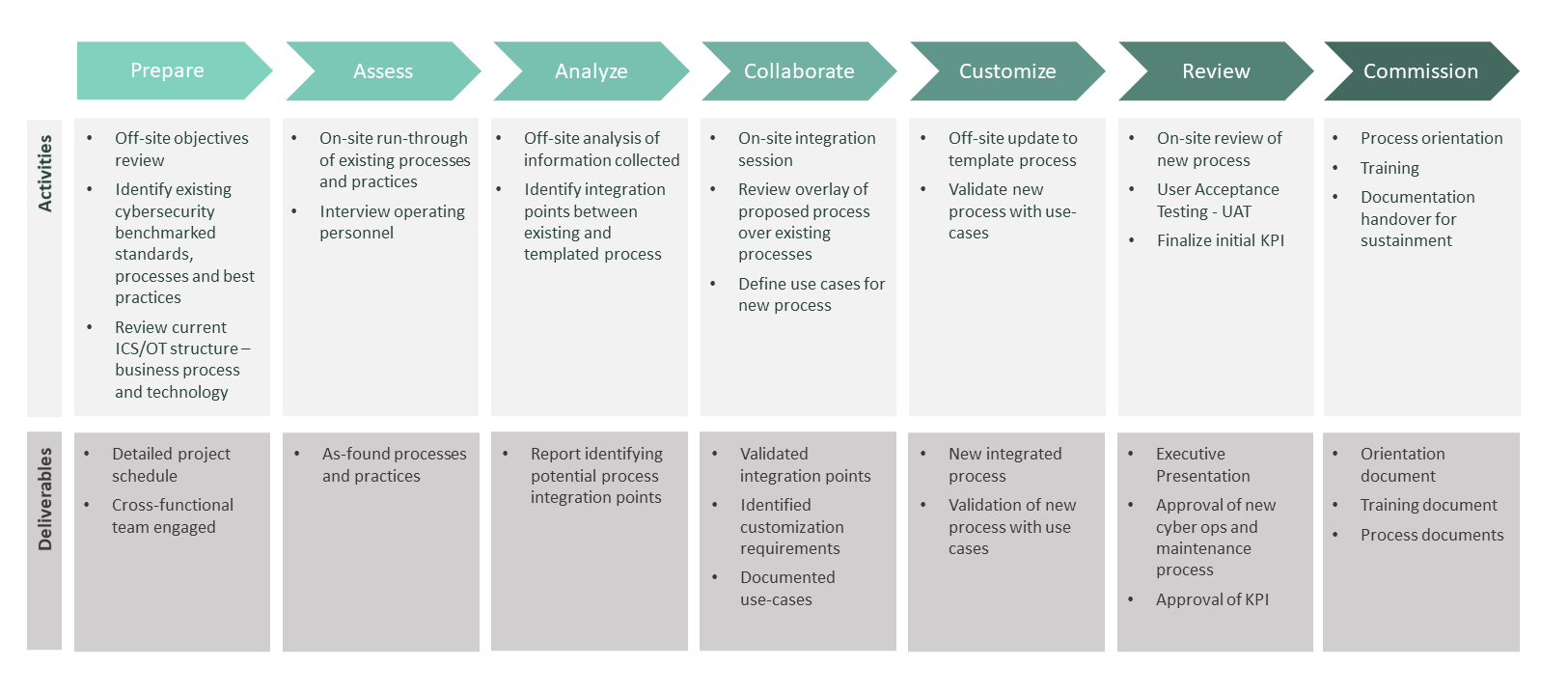
cyberORM™ SYSTEM INTEGRATION
The cyberORM™ system integration engagement consists of seven phases that are repeated for each of the Cyber ORM components.
Phase 1: Prepare. Assessment of project objectives. Review of existing cybersecurity, ICS/OT documentation.
Phase 2: Assess. In-depth assessment of existing processes.
Phase 3: Analyze. Off-site analysis to identify integration points between existing and new processes.
Phase 4: Collaborate. Collaborative on-site integration session to review existing processes, proposed process solutions, and determine use-cases.
Phase 5: Customize. Off-site analysis of the feedback received from all stakeholders to re-evaluate integration and customization updates to cyber operations and maintenance system and the integration with other cyber processes.
Phase 6: Review. On-site walk through of use-cases by select client team members and agreement on Key Performance Indicators (KPIs).
Phase 7: Commission. Present executive summary to client leadership, process orientation and training. Handover detailed process documentation.
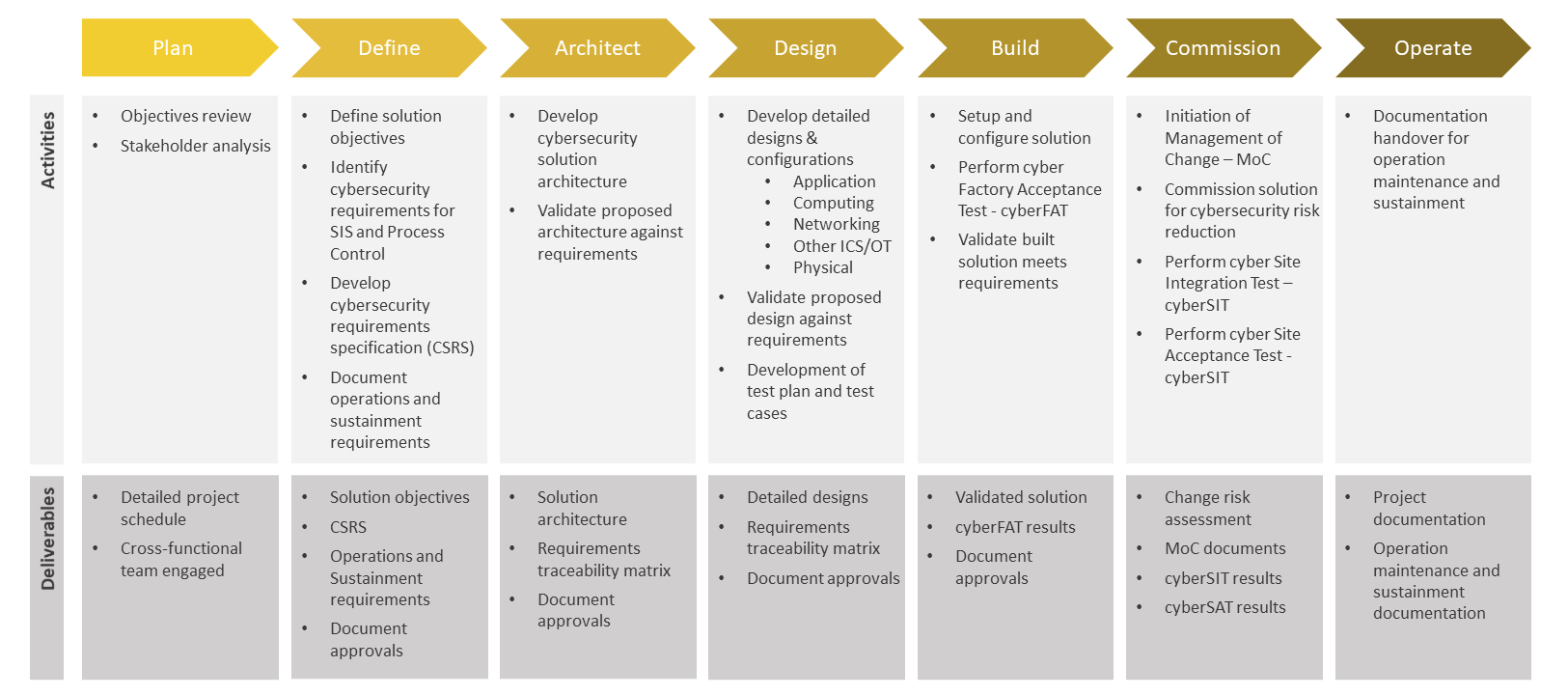
Cyber Resilience Engineering Service Delivery
Service delivery is achieved through eight phases.
Phase 1: Plan. Perform detailed stakeholder analysis and develop a project plan.
Phase 2: Define. Define solution objectives tailored to business requirements. Develop Technical Cybersecurity Requirements Specifications (CSRS) that include operating and sustainment requirements.
Phase 3: Architect. Development of cybersecurity solution architecture and validation against defined requirements.
Phase 4: Design. Development of detailed cybersecurity designs to include computing and networked devices. Establish design specifications and validate the design against defined requirements.
Phase 5: Build. Build a cybersecurity solution with associated controls. Perform Cyber Factory Acceptance Testing (CyberFAT) to validate the solution against the defined requirements.
Phase 6: Commission. Perform IT Change Management and Engineering/Plant Management of Change. Implementation of cyber countermeasures followed by Cyber Site Integration Testing (CyberSIT) and Cyber Site Acceptance Testing (CyberSAT).
Phase 7: Operate. Provide as-built detailed documentation and initiate Operations/Sustainment.