The electric and power grid is essential for the national economy since all other sectors rely on the availability of electricity. The proliferation of IoT devices, digital communications, and highly interconnected systems exposes the grid to external cyber threats. To address these new risks and challenges, organizations need to evaluate the cybersecurity risk environment and take adequate countermeasures.
Smart grids support dynamic directional information exchange between utility companies and their customers and contribute to intelligent and sustainable energy management. Despite the benefits, the power grid is also exposed to security threats inherited from the IT sector, while new vulnerabilities related to the smart grids’ nature are emerging.
Cyber attackers are increasingly leveraging these vulnerabilities to launch attacks against the grid. Attacks to electric and power grids may lead to ripple effects and cascading failures, ranging from the destruction of interconnected critical infrastructures to loss of human lives.
On 12 November 2020, cyberwatching.eu organized a webinar to discuss European funded projects that aim to secure the electric and power grid against cyber-attacks. Panagiotis Sarigiannidis, Professor at the University of Western Macedonia in Greece and member of the SDN-μSense consortium, presented a prototype solution for risk assessment using honeypots.
The goal of the SDN-microSENSE consortium is “to provide a set of secure, privacy-enabled and resilient to cyberattacks tools, thus ensuring the normal operation of Electrical Power and Energy System (EPES) as well as the integrity and the confidentiality of communications.” Other consortium members are industry leaders like Schneider Electric and Atos, and universities such as the Norwegian University of Science and Technology, and the Institute for Legal Informatics (IRI) at Leibniz Universität Hannover.
The smart grid threat landscape
The smart grid landscape contains a mix of legacy and modern digital technologies, which introduce various novel threats and vulnerabilities.
- SCADA systems, which utilize legacy industrial protocols such as Modbus, IEC 61850, and IEC104. These systems are open to severe cybersecurity flaws and vulnerabilities since they do not have the capability to integrate appropriate authentication and authorization mechanisms.
- IoT devices create critical security concerns by combining technologies such as Wireless Sensor Networks (WSNs) that introduce cybersecurity threats, such as sinkhole and wormhole cyber-attacks.
- Advanced Metering Infrastructure (AMI) is comprised of several networks and components (e.g., smart meters, data collectors, and AMI headend) that constitute an attractive target for cyber attackers. Man-in-the-Middle attacks, DDoS, and ransomware are characteristic examples.
The use of honeypots to understand cyber attackers
A honeypot is a computer system that acts as a decoy to lure cyber attackers. Security teams use them as a tool to gather intelligence on the attackers’ tactics, techniques, and procedures (TTPs) and improve the organization’s cybersecurity strategy. A honeypot supports the security team in understanding the attacker’s methodologies, learning more about known and unknown attacks, and protecting real production systems.
As a defensive mechanism, properly configured honeypots can hide and protect the real assets of the infrastructure to be protected. Honeypots find excellent application in a risk assessment process to:
- Detect potential intrusions
- Mitigate threats
- Increase threat intelligence
Honeypots in electric and power grids
According to Professor Sarigiannidis and in the context of the SDN-microSENSE project, the risk assessment process is supported by the introduction of Electrical Power and Energy Systems (EPES) Honeypots and a Honeypot Manager. The EPES honeypots aim at protecting the cyber-enabled devices by emulating their services based on the respective EPES protocols (Modbus, IEC104 and IEC 61850). On the other hand, the Honeypot Manager redirects potential abnormal events to the EPES Honeypots to identify and collect more information about them.
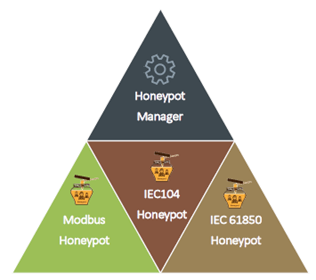
The honeypot-based risk analysis is then used to identify and apply the appropriate “islanding” security solutions in energy systems. This analysis is achieved in four steps:
- Step 1, Honeypots deployment: The honeypots are deployed emulating the behavior of real EPES devices
- Step 2, Honeypots’ Security Events: The honeypots generate security events based on their interaction with cyber attackers
- Step 3, Security Events Analysis: Security events are analyzed to identify the appropriate islanding solutions
- Step 4, Apply the Islanding Scheme: Based on the results of the analysis
What is intentional islanding?
Before we discuss applying islanding solutions to protect power and electric grids against cyber threats, it is best to understand the terminology behind these solutions.
A microgrid is a decentralized group of electricity sources and loads that is synchronized and connected to traditional wide-area grids. Microgrids can disconnect from the wide-area grid and operate autonomously in “island mode.”
Distributed Energy Resources (DERs) are resources used for electricity generation and storage, connected to the grid at a distribution level. DERs may include renewable energy sources such as solar panels and wind turbines.
The application of islanding solutions is based on the process of intentional islanding. Intentional islanding is the process where a microgrid controller disconnects a local circuit from the main power grid and forces the distributed power generators (DERs) to provide power to the entire local load.
Microgrids are core building blocks in modern energy systems, and they are used together with DERs to enable intentional islanding solutions in case of severe failures in the power grid. When a critical event occurs, such as a fault or outage of an overloaded line, it may overload additional power lines and cause subsequent outages and cascading failures. These critical events are costly and may threaten the integrity and reliability of the energy system.
Intentional islanding is used as a last resort to segment the grid into several controlled, sustainable islands and eliminate the impact of a critical fault. By minimizing the impact of critical faults, we can reduce the undesirable technical, economic, and social consequences of an imminent blackout. In case of an emergency, intentional islanding constitutes an effective solution to preserve reliable power supply in the smart distribution grid, increasing the overall system reliability.
When applying the intentional islanding process to segment the electric grid and protect against unintentional failures, specific considerations must be examined. These include the timing of applying the process, defining the appropriate island boundaries, and deciding how to implement it.
The core idea behind these considerations is to decide which transmission lines should be disconnected to create stable islands that are easy enough to control. The key objectives of the intentional islanding process should be to determine the optimal boundaries of the islands and to minimize load generation imbalance.
A solution based on deep learning methods
The SDN-microSENSE project presents a promising strategy of utilizing honeypots to drive risk-based decision-making process for electric grid segmentation and to minimize the consequences of cyber-attack. The project proposes novel islanding solutions based on capabilities offered by deep learning architectures. These solutions introduce an end-to-end deep graph neural network approach, which attempt to solve the intentional islanding problem by optimizing the load and generation balance and offering a real-time solution with increased time efficiency.
This strategy and its solutions require further collaboration between academic and industry leaders to ascertain its robust behavior in diverse, real-world situations.
Collaboration on this and similar initiatives contribute to the effective cyber threat intelligence to protect and secure the critical infrastructure against cyber threats.
ORIGNIX is your cyber-physical risk assessment partner
The introduction of IT capabilities in the Industrial Automation and Control Systems continues to increase the cyber threat landscape. ORIGNIX’s cyber Process Risk Assessment (cyberPRA) uniquely bridges IT, OT, engineering and operations risks. Our cyber Hazard and Operability (cyberHAZOP) studies augment traditional HAZOP studies by linking credible consequences to realistic cyber threat scenarios and known IT, OT, engineering and operational vulnerabilities. Keeping ahead of cyber treads and collaborating with technology partners, such as Schneider Electric and Tempered Networks, leaders in their solution segments is the cornerstone of ORIGNIX’s solutions approach. This collaboration enables building a common understanding of the challenges and developing a shared sense of ownership to deliver the most resilient solutions and the best experience for you, our clients.



